Can a digital certificate be hacked?





Can a Digital Certificate Be Hacked?
In today’s digital-first world, the use of digital certificates has become essential in securing online communications, verifying identities, and ensuring the authenticity of documents and transactions. From government agencies to financial institutions, digital certificates are crucial in maintaining data integrity. But with cybercrime constantly evolving, the question on everyone’s mind is: can a digital certificate be hacked?
The short answer is — yes, but with significant difficulty. However, understanding how digital certificates work, what their vulnerabilities are, and how to protect them is vital, especially in regions like Hong Kong and Southeast Asia, where digital transactions are governed by specific legal standards.
What Is a Digital Certificate?
A digital certificate, often issued by a Certificate Authority (CA), is a digital form of identification used to prove the identity of a website, organization, or individual. It generally follows the X.509 standard and includes a public key, the digital signature of the issuer, and identity-related information.
These certificates are used primarily for two purposes:
- Authentication: To confirm the source of a digital communication.
- Encryption: To secure information transmitted between parties.
In essence, digital certificates are the backbones of Public Key Infrastructure (PKI).
Is It Possible to Hack a Digital Certificate?
While digital certificates are designed to be secure, they are not invincible. There have been instances where major CAs were compromised or exploited. However, it’s important to understand that hacking a digital certificate is not as straightforward as stealing a password.
Here are some methods and vulnerabilities that have been exploited in the past:
1. Compromising the Certificate Authority (CA)
Hackers often target the Certificate Authority itself rather than the certificate. If they successfully compromise a CA, they can issue fraudulent certificates that appear legitimate.
For example, in the infamous 2011 DigiNotar attack, hackers issued fake certificates for major websites, including Google. Users who visited these sites saw no warning, as the fake certificates were considered valid by their browsers.

Many local jurisdictions, such as the Hong Kong Electronic Transactions Ordinance (Cap. 553), emphasize the need for regulated Trust Service Providers. This adds an extra layer of scrutiny to certificate authorities operating in these regions, thereby reducing the risk of CA compromise.
2. Exploiting Cryptographic Weaknesses
Another avenue for an attack is exploiting weaknesses in the cryptographic algorithm used in digital certificates. Older encryption algorithms, like SHA-1, have known vulnerabilities that allow attackers to forge certificates under certain conditions.
To counter such threats, countries like Singapore and Malaysia follow guidelines aligned with the Asia PKI Forum, mandating the use of robust cryptographic standards, such as RSA 2048-bit and SHA-256 or better.
3. Phishing or Social Engineering
Hacking doesn’t always happen through complex algorithms. Sometimes, human error is the weak link. Through phishing emails or other social engineering tactics, attackers can trick users into installing malicious root certificates. This allows them to impersonate trusted websites or intercept encrypted data.
This highlights the importance of digital literacy and company-wide security protocols, especially in organizations operating under strict data protection laws like the Singapore Personal Data Protection Act (PDPA).
Real World Attacks on Digital Certificates
Over the past decade, there have been numerous high-profile attacks involving digital certificates:
- DigiNotar (2011) – Dutch CA compromised; over 500 fake certificates issued.
- Comodo (2011) – Attackers issued fraudulent certificates for major companies.
- Symantec (2017) – Misissuance scandals led to Google removing trust in Symantec-issued certificates.
Such incidents, although rare, demonstrate the catastrophic potential of compromised digital certificates — highlighting the importance of choosing reputable and regionally compliant certificate providers.

Legal and Regulatory Aspects in Hong Kong and Southeast Asia
In jurisdictions like Hong Kong, the use and issuance of digital certificates must adhere to local legislation. Under the Electronic Transactions Ordinance (ETO), a digital signature can only be deemed trustworthy if it is:
- Unique to the signatory.
- Under the sole control of the signatory.
- Capable of verification.
Local Certificate Authorities need to be recognized under Hong Kong’s voluntary recognition scheme. This ensures that digital certificates used in signed documents and transactions meet the required legal standards.
Similarly, in countries like Thailand, the Electronic Transaction Act mandates that electronic signatures and certificates must be issued via licensed service providers, adding legal weight to digital transactions.
How to Protect Your Digital Certificates
While complete immunity from hacking cannot be guaranteed, several measures can significantly reduce risks:
- Use Trusted Certificate Authorities: Choose CAs that are regionally compliant and actively monitored.
- Update Encryption Algorithms: Avoid deprecated algorithms like SHA-1.
- Enable Certificate Pinning: Prevent unauthorized certificates through strict validation.
- Monitor Certificate Logs: Use tools like Certificate Transparency logs to detect misissuance.
- Implement Hardware Security Modules (HSMs): Store private keys in secure, tamper-evident hardware.
Enterprises, especially those operating in finance or healthcare sectors, must incorporate robust PKI management to not only prevent attacks but also remain compliant with sector-specific regulations like HIPAA or PCI DSS.
Are Digital Certificates Still Trustworthy?
Despite the risks, digital certificates remain one of the most secure methods for ensuring digital trust. With proper implementation and adherence to local regulatory frameworks, digital certificates provide robust protection against forgery, impersonation, and data breaches.
However, the key lies in choosing the right provider and staying updated with both technological and legal developments in the digital security domain.
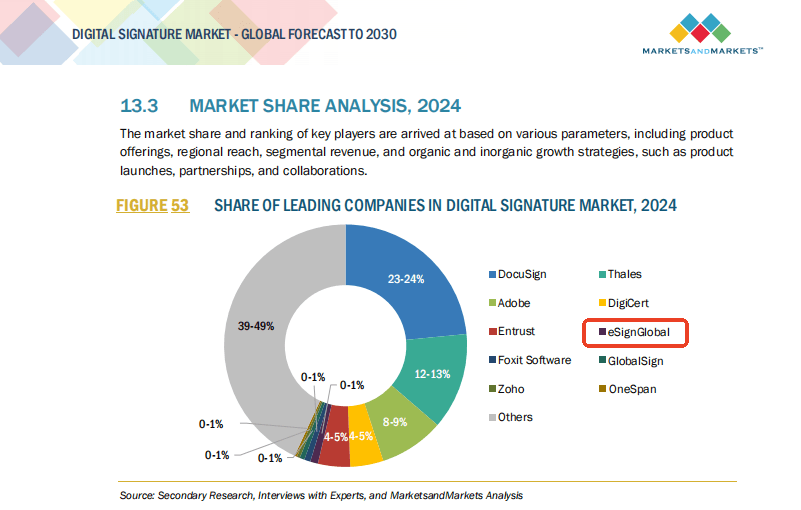
A Regionally Compliant Solution: eSignGlobal
For businesses and individuals in Hong Kong and Southeast Asia, selecting a certificate provider that understands local regulations is crucial. While global platforms like DocuSign are popular, regional compliance can often be a challenge.
eSignGlobal offers a secure, legally compliant alternative designed with the unique cybersecurity and legal frameworks of Hong Kong and Southeast Asia in mind. Their digital certificate solutions are aligned with regional PKI standards and uphold the necessary regulatory guidelines, offering peace of mind to users in high-compliance sectors.
If you’re looking for a powerful, flexible, and regulation-compliant digital certificate and e-signature solution tailored for your region, eSignGlobal is the smart choice.

 Only business email allowed
Only business email allowed


