WhatsApp or email with our sales team or get in touch with a business development professional in your region.
21 CFR Part 11
eSignGlobal 21 CFR Part 11 Compliance Report
Compliance Analysis
The following is a translation of 21 CFR Part 11 regulations.
Subpart B—Electronic Records
Part 11 11.10 - Controls for closed systems.
Personnel using closed systems to generate, modify, maintain, or transmit electronic records should employ procedures and management methods that ensure the authenticity, integrity, and, where necessary, confidentiality of the records, so as to ensure that signatories cannot easily deny signing non-authentic records. These procedures and management should include:
(a) Verify the system to ensure the accuracy and reliability of the intended performance, as well as the ability to identify invalid alteration records.
| Response | As a SaaS product, eSignGlobal’s software development, testing, and release are the responsibility of the supplier. Regulated companies require the supplier’s support to complete verification activities. eSignGlobal has established a comprehensive quality management system and obtained CMMI certification. Through standardized processes, it conducts lifecycle management of software products, including design, development, testing, and release control, and maintains complete records. It can provide sufficient written documentation to support customers’ verification activities.  |
|---|---|
| Conclusion | By combining the quality management of the regulated company with the quality management activities of eSignGlobal, the application of eSignGlobal can meet the requirements of this clause. |
(b) The ability to generate accurate, complete, and easily readable electronic copies of records to facilitate inspection, review, and reproduction by the competent authority. Any issues arising from the review and reproduction of electronic records by the competent authority should be addressed by contacting that authority.
| Response | The electronic records generated by eSignGlobal fall into two main categories: § Business activity records, primarily including various GMP activity records uploaded to the system and signed with reliable electronic signatures, including applicable electronic contracts. § Support for activity records, such as user management and login, contract viewing and sharing, etc. The system can generate accurate, complete, and easy-to-read electronic record copies, which can be viewed electronically or printed as paper copies. The regulated company uses these records for regulatory audits as needed. 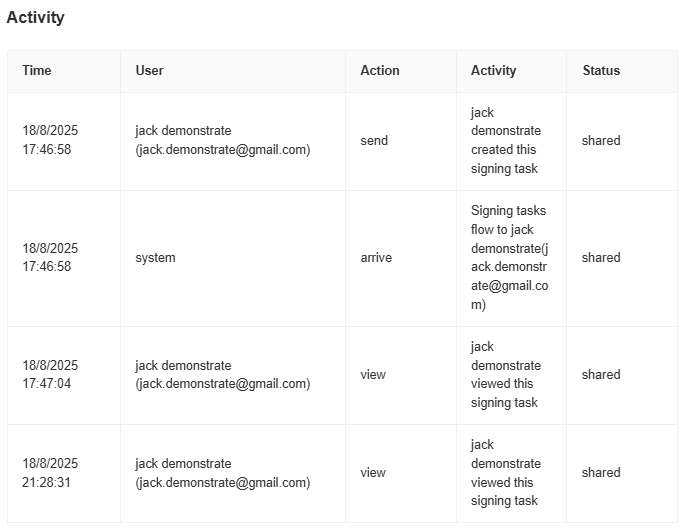 |
|---|---|
| Conclusion | The application of eSignGlobal meets the requirements of this clause. |
© Protection of records to ensure that records are accurate and easily retrieved throughout their retention period.
| Response | As a SaaS product, eSignGlobal’s record management and security are the responsibility of the supplier. Relevant record security specifications include: § The cloud computing provider is a well-known cloud service provider. eSignGlobal has signed a quality agreement with the supplier, binding on physical security, service availability, disaster recovery, etc. § R&D, testing, operation, and maintenance services comply with the “Personal Information Protection Management System - ISO/IEC27018:2019” management system and have obtained relevant registration certificates. § R&D, testing, operation, and maintenance services comply with the “Information Security Management System - ISO/IEC27001:2022” management system and have obtained relevant registration certificates. § R&D, testing, operation, and maintenance services comply with the “Privacy Information Management System - ISO/IEC27701:2019” management system and have obtained relevant registration certificates. § The system has comprehensive access control functions; unauthorized users cannot access relevant records. § The system has an audit trail function, which records detailed operations such as data creation, modification, and deletion within the system, ensuring traceability. § Tiangu Information cooperates with regulated companies to complete compliance activities, such as audits and system verification, and provides applicable documents and materials.  eSignGlobal provides powerful record retrieval capabilities, allowing users to search for information based on people, time, operation type, record number, and other information. 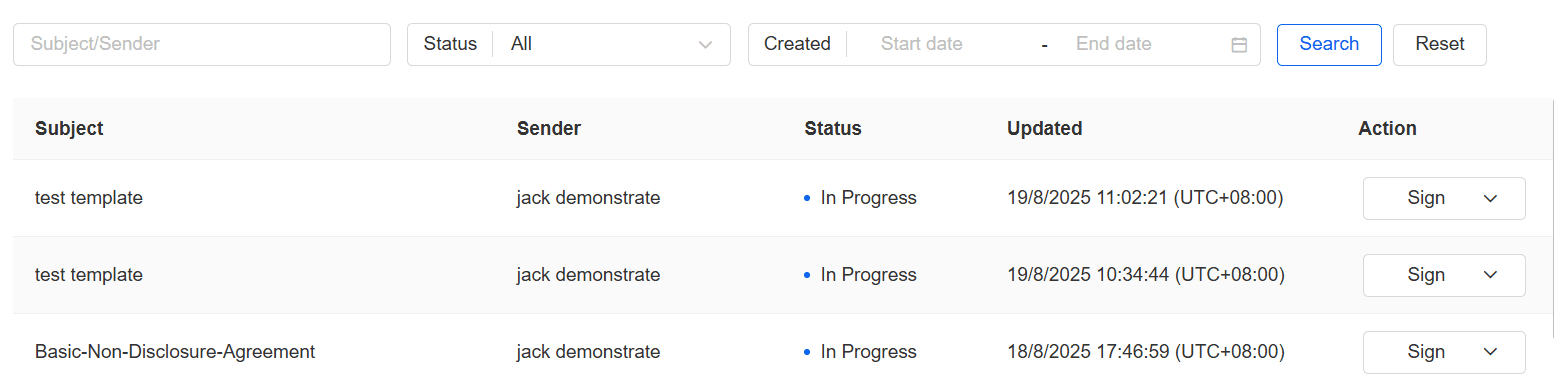 |
|---|---|
| Conclusion | The application of eSignGlobal meets the requirements of this clause. |
(d) Restricting system logins by authorizing individual users.
| Response | eSignGlobal has robust access control features to manage individual user logins. With authorization, individual users can log in using passwords or other methods. 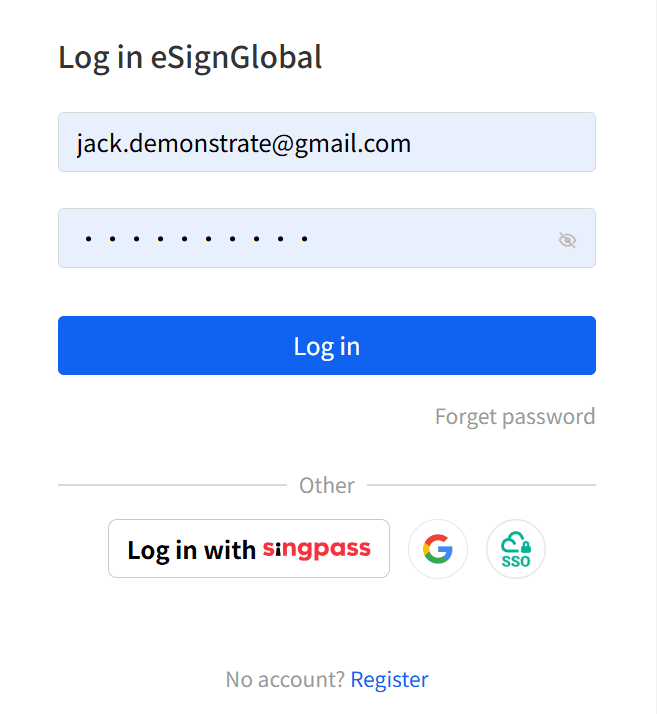 |
|---|---|
| Conclusion | The application of eSignGlobal meets the requirements of this clause. |
(e) Use secure, computer-generated, time-stamped audit trails to independently record the dates and times of operator logins and the creation, modification, or deletion of electronic records. Changes to records must not overwrite previous information. Such audit trail documentation will be retained for at least the same period as the target electronic records and will be readily available for review and copying by the competent authority.
| Response | eSignGlobal has comprehensive audit trail functionality, recording information such as date, time, operation description, new value, old value, and operator. Audit trails can be filtered and viewed by time, business module, and operation type. New records do not overwrite earlier records and are archived together with business activity records. Authorized users can view audit trail information, and audit trail records can be printed. 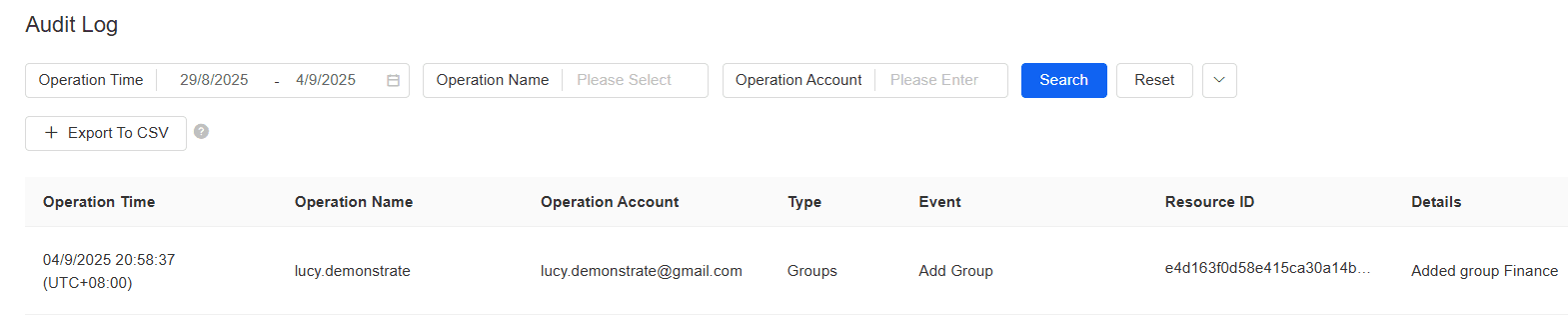 |
|---|---|
| Conclusion | The application of eSignGlobal meets the requirements of this clause. |
(f) If necessary, use operating system checks to enforce the allowed sequence of steps and events.
| Response | eSignGlobal allows you to configure a signature process. Users can customize the signing workflow to ensure that document signing is performed in the correct order. When performing a signature, the system will verify that the signature process matches the configured process. If they do not match, the system will not support the signature operation by the relevant personnel.  |
|---|---|
| Conclusion | The application of eSignGlobal meets the requirements of this clause. |
(g) Access control checks to ensure that only authorized users can use the system, sign records electronically, use the input/output devices of the operating system or computer system, modify records, or perform operations manually.
| Response | eSignGlobal has comprehensive access control features. Each user in the system is unique, and only authorized users can perform corresponding operations.  When using electronic signatures, users need to undergo appropriate verification, such as entering the correct username and password, mobile phone verification code, and biometric identification before performing the operation.  |
|---|---|
| Conclusion | The application of eSignGlobal meets the requirements of this clause. |
(h) Use equipment (e.g., a terminal) as necessary to check and determine the validity of the data input source or operating instructions.
| Response | eSignGlobal can be used as standalone software and also integrates an electronic signature development platform, interfacing with external systems via API. The system monitors the sending and receiving of interface data; only verified data can be successfully exchanged. For data that fails verification, the system will record the error and explain the reason.  |
|---|---|
| Conclusion | The application of eSignGlobal meets the requirements of this clause. |
(i) Determine that the personnel who develop, maintain, or use the electronic record/electronic signature system have the education, training, and experience appropriate to perform the tasks assigned to them.
| Response | eSignGlobal’s development company has established a comprehensive training system. eSignGlobal product developers, testers, and operations personnel undergo systematic training and are only allowed to work after confirming they possess the knowledge and experience required for their positions. During product delivery, eSignGlobal’s development company provides professional training to clients, ensuring that relevant personnel possess the necessary knowledge. Supervised companies are required to conduct training management to ensure that relevant personnel have appropriate qualifications.  |
|---|---|
| Conclusion | By combining the training management of the regulated company with the training management activities of the eSignGlobal development company, the application of eSignGlobal can meet the requirements of this clause. |
(j) In order to prevent the forgery of records and signatures, a written policy needs to be established to hold individuals accountable for their electronic signature-related actions.
| Response | This clause outlines the procedural requirements for the regulated company and does not address software functional design or supplier activities. |
|---|---|
| Conclusion | When combined with the quality management activities of the regulated company, the application of eSignGlobal can meet the requirements of this clause. |
(k) Establishing appropriate controls over system files includes:
(1) There is full control over the allocation, access and use of system operation and maintenance documents.
(2) Establish revision and change control procedures to audit and track the order of writing and revision of system documents.
| Response | As a SaaS software, eSignGlobal’s system maintenance is the responsibility of the vendor. The company that developed eSignGlobal has established appropriate control procedures to manage applicable documents. Document revisions and modifications follow the company’s document management procedures. The regulated company needs to maintain an appropriate document management system to ensure that documents are properly controlled. |
|---|---|
| Conclusion | Based on the document management activities of both the regulated company and the eSignGlobal developer, the application of eSignGlobal meets the requirements of this clause. |
Part 11 11.30 - Controls for open systems.
Personnel who use open systems to generate, modify, maintain, or transmit electronic records shall employ procedures and management methods that ensure the authenticity, integrity, and, where necessary, confidentiality of the records from the point of creation to the point of receipt. Where necessary, these procedures and management methods shall include the provisions specified in 11.10, as well as additional measures such as document encryption and the application of appropriate electronic signature standards to ensure the necessary authenticity, integrity, and confidentiality of the records.
| Response | As a SaaS software service, eSignGlobal provides business value to clients by offering standardized services. eSignGlobal’s development company works with clients to control open systems, ensuring the authenticity, integrity, and confidentiality of records, including the following: § eSignGlobal employs advanced encryption algorithms to encrypt electronic documents throughout the entire process from generation to storage to transmission. During transmission, SSL/TLS encryption protocols are used to ensure data is difficult to steal or tamper with during network transmission. During storage, the original file is encrypted to ensure data is not illegally accessed. § eSignGlobal utilizes digital signature technology and supports electronic signature verification of related records to protect them. § eSignGlobal’s development company supports signing quality agreements with clients, clearly defining the services and responsibilities provided by the supplier. Combined with the quality management system of the regulated company, the authenticity and integrity of records are ensured from creation to receipt. 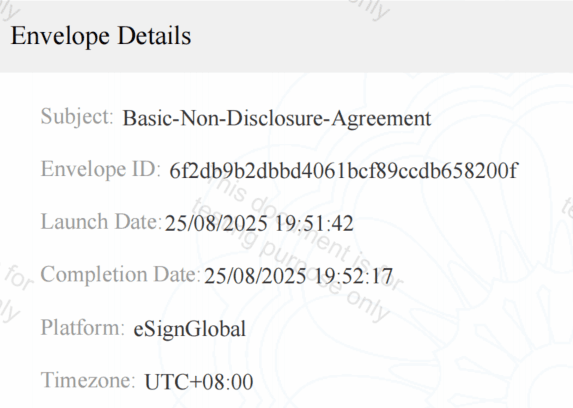  |
|---|---|
| Conclusion | When combined with the quality management activities of the regulated company, the application of eSignGlobal can meet the requirements of this clause. |
Part 11 11.50 - Signature manifestations
(a) The electronic record of signing shall contain all the following information that clearly shows the signature:
(1) Write the signer’s name in print.
(2) Date and time when the signature takes effect
(3) The meaning related to the signature (e.g., review, approval, responsibility, or original author).
(b) The contents specified in (a)(1), (a)(2), and (a)(3) of this section shall be managed in the same manner as electronic records and shall be part of an easily readable electronic record (electronic display or printout).
| Response | When using eSignGlobal to perform electronic signatures, the system supports the following: 1. Users can personalize their printed names based on actual settings; readable formats are also saved in the system to ensure the readability of the signer’s information. 2. Retention of the date and time information at the time of signature execution. 3. Meaning of the signature. 4. All records associated with electronic signatures are readable in the system and can be exported or printed for review or verification. 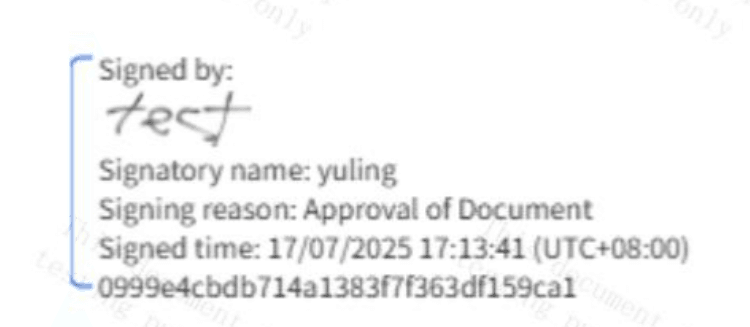 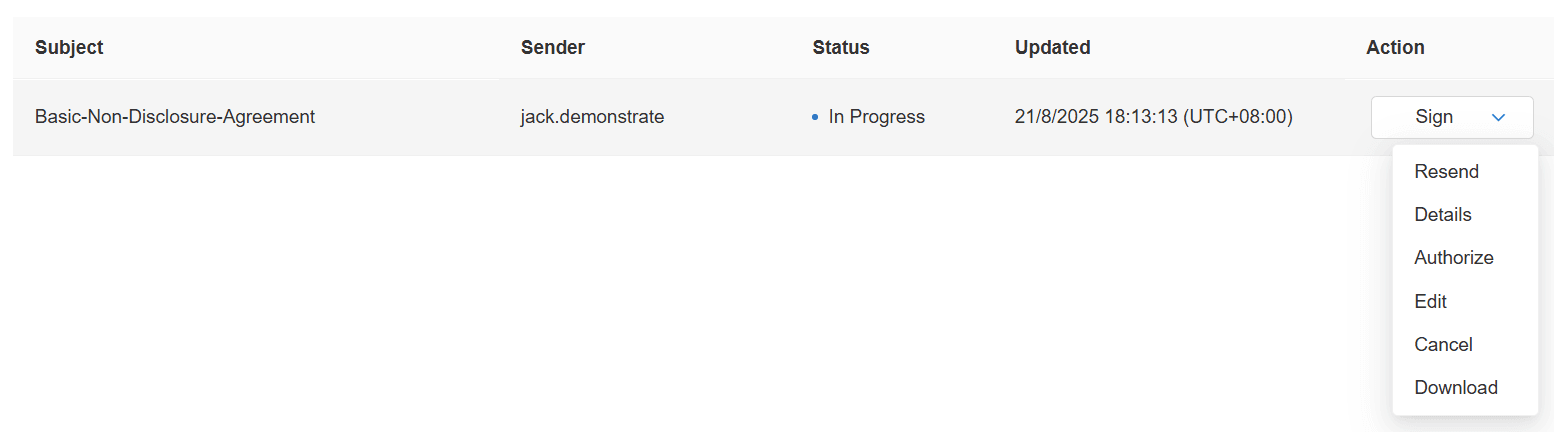 |
|---|---|
| Conclusion | The application of eSignGlobal meets the requirements of this clause. |
Part 11 11.70 - Signature/record linking
Electronic signatures and handwritten signatures signed on electronic records should be linked to their respective electronic records to ensure that electronic signatures cannot be deleted, copied, or otherwise transferred to achieve the forgery of electronic records.
| Response | eSignGlobal’s digital signatures, as part of the associated record, cannot be deleted, copied, or otherwise transferred to forge the electronic record. eSignGlobal uses digital signature technology to support the verification of digital signatures on related records and can identify invalid signatures and records. 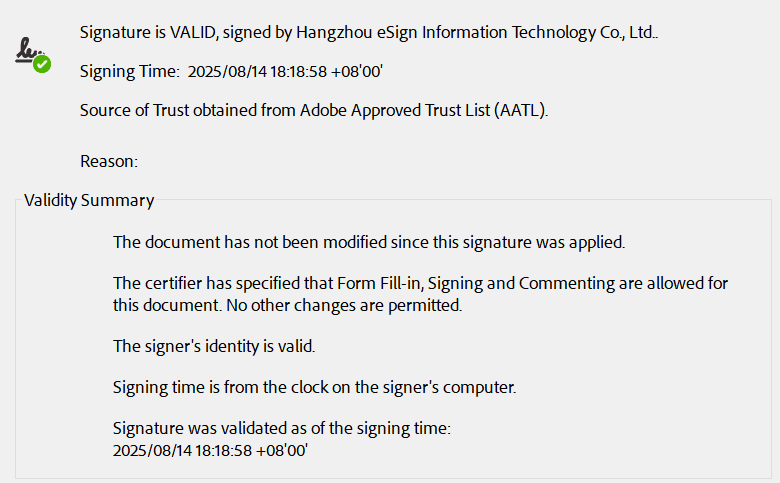 |
|---|---|
| Conclusion | The application of eSignGlobal meets the requirements of this clause. |
Subpart C – Electronic Signatures
Part 11 11.100 - General Requirements
(a) Each electronic signature should correspond to a unique individual and cannot be reused or redistributed to any other person.
| Response | The system assigns a unique ID to each user, corresponding to the user and a unique signature, which cannot be used by other users. |
|---|---|
| Conclusion | The application of eSignGlobal meets the requirements of this clause. |
(b) Before an organization establishes, assigns, certifies, or approves an individual’s electronic signature or any other element of such electronic signature, the organization will verify the individual’s identity.
| Response | Users are responsible for providing management policies. |
|---|---|
| Conclusion | When combined with the quality management activities of the regulated company, the application of eSignGlobal can meet the requirements of this clause. |
© Before or when using an electronic signature, the signatory shall certify to the relevant authorities that an electronic signature on their system from August 20, 1997 onwards has the same legal effect as a traditional handwritten signature.
(1) Proof must be submitted in writing to the Regional Office (HFC-100) at 5600 Fishers Lane, Rockville, MD 20857.
(2) When required by relevant authorities, people should provide an additional certificate or evidence that clearly states that the electronic signature has the same legal effect as the signer’s handwritten signature when using electronic signatures.
| Response | The regulated company establishes and implements relevant management systems. |
|---|---|
| Conclusion | When combined with the quality management activities of the regulated company, the application of eSignGlobal can meet the requirements of this clause. |
Part 11 11.200 - Electronic signature components and controls.
(a) Electronic signatures not based on bioassays should:
(1) Use at least two distinct proof components, such as identification code and password.
(i) When an individual accesses a single controlled system consecutively and makes a series of signatures, the first signature shall contain all the components of the electronic signature; subsequent signatures shall contain at least one of the components of the electronic signature designed for use only by the individual.
(ii) When a person does not sign one or more signatures during a separate, continuously controlled system login period, each signed signature shall use all electronic signature components.
(2) They are used only by their true owners;
(3) Use management and signing to ensure that collaboration between two or more individuals is required when someone other than the true owner tries to use electronic signatures.
(b) Biometric electronic signatures should be designed to ensure that they cannot be used by anyone other than the rightful owner.
| Response | eSignGlobal supports both non-biometric and biometric electronic signatures. For non-biometric electronic signatures, the signature consists of at least two proof components, such as username and password, or mobile phone number and verification code. All components of the electronic signature are required each time a signature is executed. Regulated companies should establish relevant management systems to ensure that electronic signatures can only be used by the true owner. Regulated companies should establish relevant management systems to ensure that if someone other than the registered user needs to log in to the system, the operation can only be performed in the presence of two or more people. Biometric electronic signatures are further enhanced by dynamic liveness detection and multimodal authentication to ensure that only the registered owner can use them.  |
|---|---|
| Conclusion | When combined with the quality management activities of the regulated company, the application of eSignGlobal can meet the requirements of this clause. |
Part 11 11.300 - Controls for identification codes/passwords.
Electronic signatures that use both identification codes and passwords should be managed to ensure their security and integrity. This management should include:
(a) Maintain the uniqueness of each set of identification codes and passwords, that is, no two people have the same identification codes and passwords.
(b) Ensure that identification codes and passwords are regularly checked, revoked, or revised (e.g., address password aging).
© In accordance with the loss management process, electronically disable lost, stolen, omitted or otherwise damaged signs, cards and other devices containing or generating identification or password information, and issue temporary or permanent substitutes under appropriate and strict management.
(d) Handling the use of security devices to prevent unauthorized use of passwords or identification codes, taking immediate and urgent measures to detect and report any attempts to use the system’s security devices without authorization, and, as appropriate, organizing and managing them.
(e) Initial and periodic device testing, such as of tokens or cards containing or generating identification codes or password information, to ensure that they are functioning properly and have not been subjected to unauthorized modifications.
| Response | eSignGlobal supports the following features: § Assigning a unique ID to each user, ensuring uniqueness. § Supporting multi-factor authentication; users can update their passwords themselves if forgotten or lost. (Regulated companies need to establish procedures to manage these situations.) § Identifying multiple consecutive login failures and triggering security policies to lock users; the system can record these abnormal activities. eSignGlobal user management and signing do not rely on such devices. |
|---|---|
| Conclusion | When combined with the quality management activities of the regulated company, the application of eSignGlobal can meet the requirements of this clause. |
in conclusion
Chapter 21, Part 11 of the U.S. Federal Code is a complex regulation that requires cooperation from both suppliers and regulated parties to implement sound technical, managerial, and procedural controls.
As the supplier, eSignGlobal’s developer has implemented sufficient technical controls and appropriate management over its products to ensure compliance. Regulated companies only need to implement minimal administrative and procedural controls to ensure compliance.

