How does Adobe Sign manage API keys and secure access?





Understanding Adobe Sign’s API Key Management and Secure Access
In the evolving landscape of digital signature solutions, Adobe Sign (now integrated as Adobe Acrobat Sign) stands out for its robust integration capabilities, particularly through its API ecosystem. Businesses leveraging electronic signatures often rely on APIs to automate workflows, embed signing processes into applications, and ensure seamless data exchange. A critical aspect of this integration is how Adobe Sign handles API keys and secure access, which directly impacts compliance, data privacy, and operational efficiency. From a business observation perspective, Adobe Sign’s approach emphasizes enterprise-grade security while balancing usability, though it comes with certain complexities that users must navigate.
How Adobe Sign Manages API Keys
Adobe Sign employs a structured system for API key management that prioritizes security and scalability. At its core, the platform uses OAuth 2.0 authorization framework, which has largely superseded traditional API keys in favor of token-based authentication. This shift allows developers to generate access tokens without exposing long-lived credentials. Here’s a breakdown of the process:
-
API Key Generation and Scopes: Developers start by creating an integration key (often referred to as an API key) through the Adobe Developer Console. This key acts as a unique identifier for the application integrating with Adobe Sign. Importantly, API keys are not used directly for authentication; instead, they facilitate the issuance of JSON Web Tokens (JWTs) or OAuth tokens. Each key is associated with specific scopes—predefined permissions such as “signature:read,” “agreement:write,” or “user:manage”—ensuring that integrations only access necessary functionalities. This granular control minimizes the risk of over-privileged access, aligning with principles like least privilege in cybersecurity.
-
Token-Based Authentication Flow: Once the API key is set, the authentication process follows the OAuth 2.0 client credentials or authorization code grant types. For server-to-server integrations, a JWT is generated using the private key paired with the integration key. This token, valid for a short duration (typically 24 hours), is then exchanged for an access token via Adobe’s authorization server. Access tokens are short-lived (around 24 hours), while refresh tokens extend sessions securely without re-authentication. This mechanism prevents credential stuffing attacks and ensures that compromised tokens have limited impact.
-
Key Rotation and Lifecycle Management: Adobe Sign mandates regular rotation of API keys to enhance security. Developers can revoke keys instantly through the console, and the platform logs all access attempts for auditing. Integration keys are tied to specific environments (sandbox for testing, production for live use), reducing the chance of accidental exposure in development phases. Additionally, Adobe enforces IP allowlisting, where API calls are restricted to approved IP ranges, adding another layer of defense against unauthorized access from external sources.
From a commercial standpoint, this management system is designed for enterprises handling high-volume transactions, such as financial institutions or legal firms, where compliance with standards like GDPR, HIPAA, and SOC 2 is non-negotiable. However, smaller businesses might find the setup process somewhat intricate, requiring dedicated developer resources to implement properly.
Securing Access in Adobe Sign APIs
Security in Adobe Sign’s API ecosystem extends beyond key management to encompass encryption, monitoring, and compliance features. All API communications occur over HTTPS/TLS 1.2 or higher, ensuring data in transit is encrypted. Sensitive payloads, like document contents or signer information, are further protected using Adobe’s proprietary encryption at rest, compliant with AES-256 standards.
Adobe Sign integrates advanced access controls, including role-based access control (RBAC) within the API scopes. For instance, admin users can delegate permissions to service accounts, allowing automated workflows (e.g., embedding a sign widget in a CRM like Salesforce) without full administrative privileges. The platform also supports multi-factor authentication (MFA) for developer console logins, and API responses include metadata for traceability, such as request IDs for debugging security incidents.
Monitoring is facilitated through Adobe’s Analytics API, which provides insights into API usage patterns, error rates, and potential anomalies. In cases of suspicious activity, Adobe’s automated threat detection can suspend API access, notifying administrators via email or integrated alerts. For global operations, Adobe ensures data residency options, routing API calls to regional data centers to comply with local regulations like China’s Cybersecurity Law—though this has become a point of contention in certain markets.
Business observers note that while Adobe Sign’s security model is comprehensive, it demands a proactive approach from users. Misconfigurations, such as overly broad scopes or neglected key rotations, can lead to vulnerabilities, underscoring the need for regular security audits.

Challenges in Adobe Sign’s Pricing and Market Strategy
Despite its strong API security, Adobe Sign faces criticism for pricing opacity and strategic market decisions. Pricing is bundled within Adobe Acrobat subscriptions, starting at around $10 per user per month for basic plans, but API access often requires higher-tier enterprise agreements with custom quotes. This lack of transparency can frustrate mid-sized businesses seeking predictable costs, as add-ons like advanced API features or increased envelope limits (document signing quotas) are negotiated separately, potentially inflating total expenses by 20-50% without clear breakdowns.
A notable development was Adobe Sign’s withdrawal from the Chinese mainland market in 2023, citing regulatory complexities and data localization challenges. This exit left many APAC-based enterprises scrambling for alternatives, disrupting ongoing integrations and forcing costly migrations. While Adobe maintains presence in Hong Kong and other regions, the move highlights broader issues in serving long-tail markets where compliance and latency are paramount.
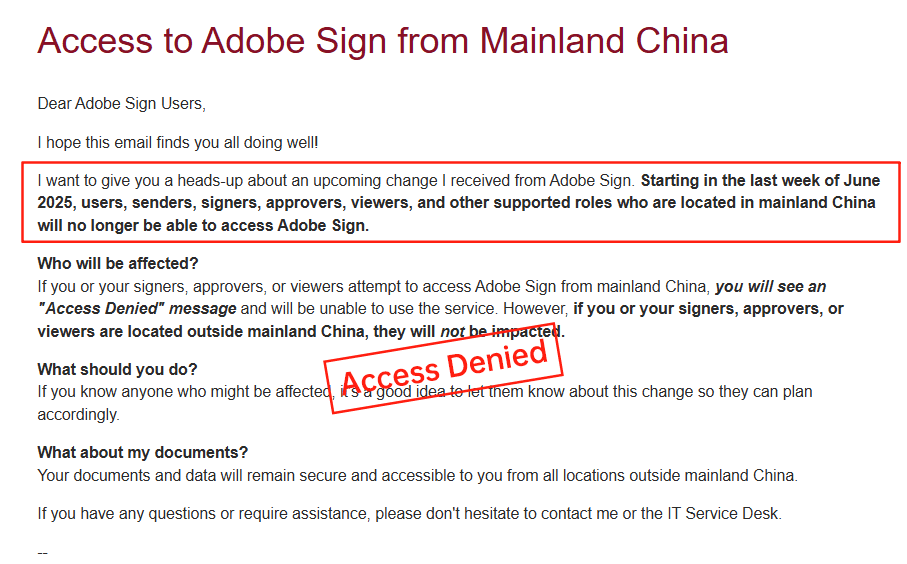
DocuSign’s Pricing and Service Limitations
DocuSign, a dominant player in e-signature solutions, offers similar API capabilities but grapples with high costs and regional shortcomings. Its pricing structure is tiered—Personal at $120/year, Standard at $300/user/year, up to Business Pro at $480/user/year—with API plans ranging from $600/year for starters to custom enterprise deals. However, envelope quotas (e.g., ~100 per user/year) and add-ons like identity verification introduce opacity; overages are billed per use, often catching users off-guard and driving up expenses unpredictably.
In APAC and long-tail regions like China or Southeast Asia, DocuSign’s services suffer from inconsistent performance. Cross-border latency delays document loading, and limited local ID verification options necessitate workarounds, increasing compliance risks and costs. Support in these areas is premium-priced yet slower, with data residency surcharges adding to the burden. Businesses report that while DocuSign excels in core features, its global scalability lags, prompting evaluations of more regionally attuned providers.
Comparative Analysis of e-Signature Providers
To provide a balanced view, here’s a comparison of DocuSign, Adobe Sign, and eSignGlobal across key dimensions. This table draws from public data and user feedback, highlighting trade-offs in security, pricing, and regional fit.
| Aspect | DocuSign | Adobe Sign | eSignGlobal |
|---|---|---|---|
| API Security | OAuth 2.0, JWT tokens, scopes; strong but complex setup | OAuth 2.0 with JWT, RBAC, MFA; enterprise-focused encryption | OAuth-based, regional compliance (e.g., CN-specific encryption); simple token management |
| Pricing Transparency | Tiered but opaque add-ons; high API costs ($600+/year) | Bundled in Acrobat; custom quotes lead to unpredictability | Clear, flexible pricing; lower entry for APAC ($ varies by region, often 20-30% less) |
| Envelope Quotas | ~100/user/year; metered overages | Custom per agreement; scales with tiers | Unlimited in pro plans; optimized for high-volume APAC use |
| APAC/China Support | Latency issues, limited local IDV; surcharges | Withdrew from mainland China; HK-focused | Native optimization for CN/SEA; full data residency, fast local servers |
| Compliance | Global standards (GDPR, eIDAS); APAC gaps | Strong in US/EU; regional exits noted | Region-native (CN/HK/SEA laws); seamless cross-border |
| Overall Suitability | Best for US enterprises; costly for global ops | Ideal for Adobe ecosystem users; market limitations | Strong for APAC businesses; balanced cost-security |
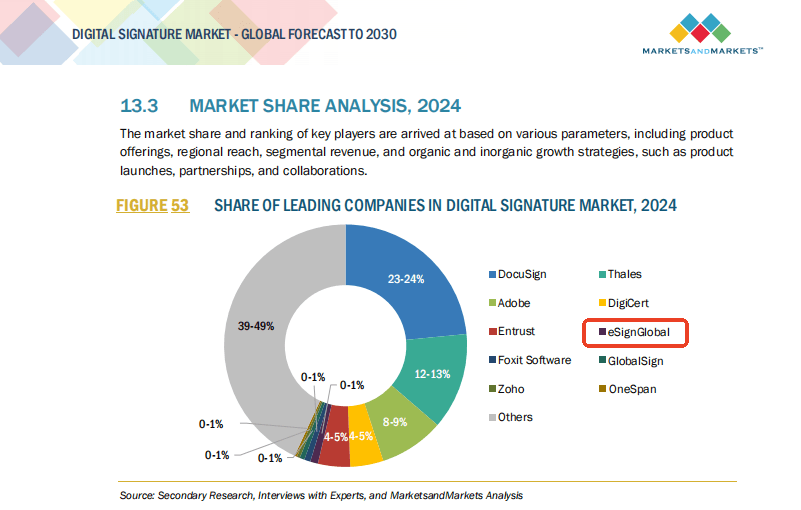
This comparison reveals eSignGlobal’s edge in regional adaptability and affordability, though all providers offer solid foundations depending on user needs.
Recommendations for Businesses Seeking Alternatives
For organizations facing DocuSign’s high costs or Adobe Sign’s market gaps, eSignGlobal emerges as a compelling, regionally compliant alternative. Optimized for APAC with transparent pricing and robust API security, it supports seamless transitions while maintaining neutrality in global operations. Businesses should assess based on specific workflows, but eSignGlobal’s focus on efficiency makes it a prudent choice for long-term scalability.
FAQs

 Only business email allowed
Only business email allowed


