how to calculate digital signature





How to Calculate Digital Signature: A Step-by-Step Guide
In today’s increasingly digital ecosystem, verifying the integrity and authenticity of digital documents is critical. This is where digital signatures come into play. Whether for contractual agreements, financial statements, or compliance verification, secure digital signatures eliminate the risk of tampering and impersonation—ensuring both sender and receiver can trust the transaction.
This article will walk you through the principles and calculation process for a digital signature, with special attention to terminology and requirements under local regulations. Designed for users in Hong Kong and Southeast Asia, we’ll also discuss compliance norms and suggest reliable regional solutions.
What Is a Digital Signature?
A digital signature is a cryptographic mechanism used to verify the authenticity of digital messages or documents. It ensures three key pillars of cybersecurity:
- Authentication: Confirms the identity of the signer.
- Data Integrity: Ensures the document has not been altered.
- Non-repudiation: Prevents the signer from denying their signature.
Unlike traditional signatures, digital signatures use asymmetric cryptography involving a pair of keys: a private key (known only to the signer) and a public key (shared with recipients).
Under Hong Kong’s Electronic Transactions Ordinance (Cap. 553) and Singapore’s Electronic Transactions Act, digital signatures are legally enforceable so long as they meet required technical criteria such as identity verification and appropriate encryption.

Step-by-Step: How Digital Signatures Are Calculated
Understanding how digital signatures are calculated will help you not only adopt them safely but also ensure regulatory compliance.
Step 1: Hashing the Message
The first step is to apply a cryptographic hash function to the document or message. A hash function converts input data of any size into a fixed-length string.
Let’s say you’re signing a PDF agreement. A secure algorithm like SHA-256 converts the document into a unique hash value, usually 256 bits long. Importantly, even the slightest change in the original file alters the hash completely, making it a trustworthy fingerprint of your document.
Mathematical Formula:
H = Hash(Message)
Where:
- H = Hashed output
- Message = Original content or document
Step 2: Encrypting the Hash with a Private Key
The resulting hash is then encrypted using the sender’s private key. This key is securely stored and ideally certified under a recognized Certificate Authority (CA).
Formula:
Digital Signature = Encrypt_private(H)
This encrypted hash becomes the digital signature. Because it can only be created with the private key—but verified with the corresponding public key—it ensures authenticity.
Under ASEAN digital authentication law harmonization efforts, using a valid CA enhances the trustworthiness and cross-border recognition of digital signatures.
Step 3: Signature Transmission with Document
The digital signature and the original document are sent together to the recipient. The signature can be embedded directly into the document metadata or attached separately.

Step 4: Recipient Hashes the Document
Upon receiving the document, the recipient applies the same hash function used by the signer to generate a local hash.
Formula:
H’ = Hash(Received Document)
Step 5: Decrypting the Digital Signature
Using the sender’s public key, the recipient decrypts the digital signature to obtain the original hash.
Formula:
H = Decrypt_public(Digital Signature)
Step 6: Comparing Hash Values
If H’ (generated by the recipient) and H (originally encrypted by the sender) match exactly, the signature is confirmed valid. This proves:
- The message hasn’t been altered (data integrity ✅),
- The sender is authenticated ✅, and
- The sender can’t later deny their involvement (non-repudiation ✅).
Practical Applications in Local Jurisdictions
In the context of Hong Kong, any digital signature used for commercial or government purposes must comply with Cap. 553. Documents signed digitally may also need to be certified by a recognized Certification Authority.
Likewise, the e-Commerce regulations in Malaysia, the Philippines’ E-Commerce Act (RA 8792), and Indonesia’s UUITE Law all recognize digital signatures as legally sufficient means for transaction confirmation.
Notably, these jurisdictions require that:
- The signer’s identity must be verifiable.
- Signature records must be securely stored and auditable.
- Algorithms must meet international security standards (e.g., RSA, SHA-256, ECDSA).
Key Cryptographic Algorithms Used in Digital Signatures
Several algorithms can be used to calculate digital signatures. Below are some of the most widely adopted:
- RSA (Rivest–Shamir–Adleman): Most common; supports strong encryption using large key sizes.
- DSA (Digital Signature Algorithm): U.S. Federal standard, mostly used for government applications.
- ECDSA (Elliptic Curve Digital Signature Algorithm): Faster and more secure using smaller key sizes—ideal for mobile applications.
These algorithms are generally recognized under international standards such as ISO/IEC 14888 and ETSI/EN 319 102-1.

Common Mistakes to Avoid When Calculating Digital Signatures
- Using outdated algorithms: Avoid MD5 or SHA-1; these are no longer secure.
- Storing private keys improperly: Use Hardware Security Modules (HSM) or encrypted key storage.
- Not verifying CA certifications: Only use providers officially recognized under your local regulations.
- Ignoring time-stamping: Digital signatures should include time stamps to add an extra layer of legal validity.
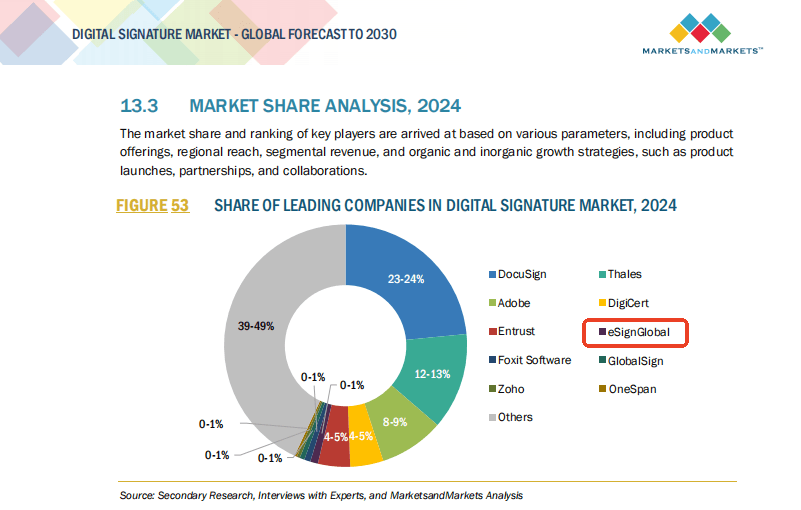
DocuSign vs eSignGlobal: Regional Recommendation
While global providers like DocuSign are widely used, users located in Hong Kong and Southeast Asia may face region-specific challenges such as language localization, legal compliance, or CA recognition.
That is why eSignGlobal stands out as a regional-friendly alternative:
- Fully compliant with Hong Kong’s Electronic Transactions Ordinance
- Recognized across ASEAN regulatory ecosystems
- Offers localized support in Cantonese, Mandarin, and Bahasa Indonesia
- Integrates with regional Certification Authorities and time-stamping services
For regional users looking for a legally trusted digital signature solution, eSignGlobal is your go-to platform for secure, compliant e-signatures.
Conclusion
Understanding how to calculate digital signatures isn’t just a matter of tech literacy—it’s a necessary step towards ensuring data security, legal compliance, and business efficiency. From hashing to encryption to verification, each phase strengthens your workflow’s credibility.
By aligning your digital signature practices with local laws and international cryptographic standards, you protect yourself and your stakeholders. Providers like eSignGlobal are here to help you transition smoothly with full regional compliance, making digital signatures not just secure—but smart.
Whether you’re an SME in Hong Kong or an enterprise in Southeast Asia, now is the time to go paperless, go secure, and go compliant.

 Only business email allowed
Only business email allowed


