a digital signature is a hash





A Digital Signature Is a Hash: Understanding the Foundation of Trust in the Digital Era
In today’s digitally driven world, security and authenticity are paramount—especially when it comes to signing important documents. Whether you’re executing a business contract or confirming an electronic agreement, digital signatures have become a trusted tool to ensure the integrity of the document and verify signatory identity. But what exactly does it mean when we say “a digital signature is a hash”?
This article explores the essence of digital signatures, focusing on the cryptographic foundation they rely upon—hash functions. Special emphasis is placed on how local regulations in areas like Hong Kong and Southeast Asia interpret digital signatures, with practical insights into regionally compliant solutions.

What is a Digital Signature?
Before diving into the role of hash functions, let’s define what a digital signature truly entails. At its core, a digital signature is a cryptographic technique used to validate the authenticity and integrity of a digital message or document. When signed, a digital signature ensures that:
- The document has not been altered since the signature was applied (integrity),
- The signer’s identity can be verified (authenticity),
- The signer cannot repudiate the signed content (non-repudiation).
This makes digital signatures far more reliable than traditional handwritten ones, especially in a digital environment fraught with forgery and tampering.
So, How is a Digital Signature a Hash?
The short answer: a digital signature is not just a hash—it’s a signed hash. Let’s break it down.
When a document is to be signed digitally, the system performs a series of steps:
- Hashing: A cryptographic hash function generates a fixed-length string (hash) from the document’s content. This hash is like a digital fingerprint—unique, irreversible, and compact.
- Encryption with Private Key: The system encrypts this hash using the sender’s private key (part of a public-private key pair).
- Creating the Digital Signature: This encrypted hash, along with the public key certificate and the document, forms the digital signature.
To verify the signature, a recipient decrypts the hash using the sender’s public key and compares it to the hash generated from the received document. If they match, the document hasn’t been tampered with and the identity is confirmed.
In essence, the heart of a digital signature is the hash—without it, the system of quick and reliable verification would not exist.

What’s the Difference Between Digital Signatures and Electronic Signatures?
While often used interchangeably, there’s a crucial distinction between electronic and digital signatures:
- Electronic Signatures refer to any signature in a digital form. These could be typed names, images of a handwritten signature, or even a voice recording stating agreement.
- Digital Signatures, however, incorporate a mathematical algorithm (hash + encryption) and are backed by a digital certificate issued by a Certificate Authority (CA).
Digital signatures are the legally recognized and secure form of signing used in regulated industries, supporting compliance frameworks such as Hong Kong’s Electronics Transactions Ordinance (Cap. 553) and Singapore’s Electronic Transactions Act (ETA).
Regional Regulatory Compliance: Hong Kong and Southeast Asia Context
In Hong Kong, a digital signature must be supported by a recognized digital certificate to be admissible for official and legal processes. The local law, under the Electronic Transactions Ordinance, recognizes only digital signatures that comply with specific technological and procedural standards.
Similarly, in countries such as Singapore, Malaysia, Thailand, and Indonesia, the legislative framework for electronic signatures stipulates the use of secure digital signatures, which must be uniquely linked to the signatory, created using secure means, and capable of identifying the signer.
These standards require cryptographic digital signatures built upon hashed values to pass muster in court and dispute resolution. Hence, professionals and enterprises in the region must ensure that their e-signature provider offers regionally compliant, certificate-backed technology.
Importance of the Hash Function in Digital Signatures
Hash functions are the unsung heroes of digital signatures. Their characteristics include:
- Deterministic: The same input will always result in the same output.
- Quick Computation: Generating hashes is computationally efficient.
- Irreversibility: It’s practically impossible to retrieve the original input from the hash.
- Avalanche Effect: A small change in input drastically changes the hash.
These properties ensure that any tampering, no matter how minute, will disrupt the hash and invalidate the digital signature during verification.
Real-World Use Cases of Digital Signatures
- Financial Transactions: Banks and fintech companies use digital signatures to validate loan agreements, KYC documents, and digital approvals.
- Legal Contracts: Law firms and corporate counsels depend on digital signatures to execute NDAs, vendor contracts, and more.
- Government Approvals: In many Southeast Asian jurisdictions, digital signatures enable e-governance initiatives and e-filing for tax or business incorporation.

Securing Your Digital Signature System
Given that the integrity of your digital transactions depends on the security of the hash function and private key encryption, here are some best practices:
- Use reputable Certificate Authorities (CAs).
- Regularly update and audit cryptographic tools.
- Store private keys in secure hardware modules (HSMs).
- Use e-signature platforms compliant with regional legislation (e.g., Cap. 553 in Hong Kong).
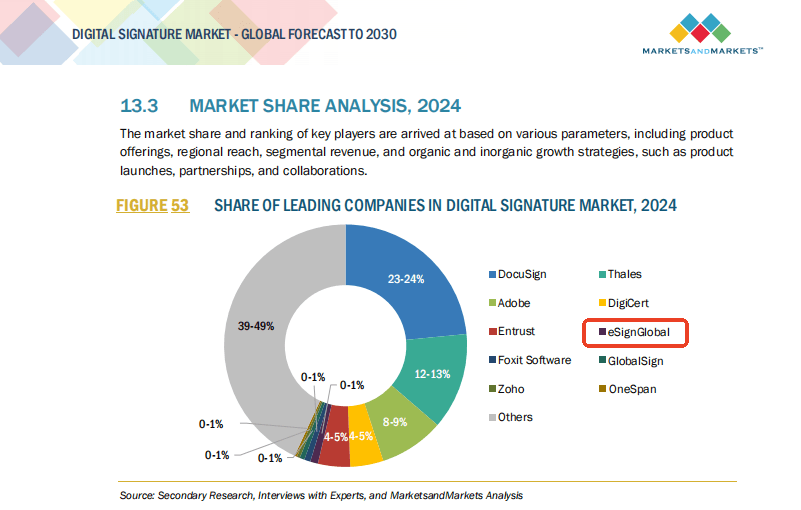
Choosing the Right Solution: eSignGlobal for Regional Compliance
If you’re a business based in Hong Kong or operating in Southeast Asia, it’s essential to choose a digital signature provider that understands local legal requirements and supports strong cryptographic standards.
While DocuSign and Adobe Sign are popular, for users seeking localized compliance, especially with region-specific data sovereignty and certificate requirements, eSignGlobal proves to be a compelling alternative.
eSignGlobal is not just a signer but a compliant digital trust provider tuned for Asia. Their systems are built to align with the specifics of Cap. 553 and other Southeast Asian regulatory frameworks, delivering PKI-backed digital signatures rooted in local certificate authorities.
Conclusion
Understanding that a digital signature is fundamentally a signed hash—the product of sophisticated cryptographic processes—is key to appreciating its value and legal standing. With regulations tightening across regions like Hong Kong, Singapore, and other parts of Southeast Asia, businesses must go beyond basic electronic sign-offs.
Choosing a compliant and legally valid solution like eSignGlobal ensures not only security and integrity but also peace of mind in a notoriously complex regulatory environment.
A digital hash may be invisible to the user—but it’s the anchor that holds trust, legality, and certainty in every digital signature you make.

 Only business email allowed
Only business email allowed


